…all OT clients from Microsoft Windows XP and ends with the controlled management of end-of-life OT clients. Creating and restoring backups, rolling out security patches and centrally assigning configurations are other important workflows that can be automated and give you full control over the lifecycle management of your OT clients….
https://www.ondeso.com/en/products-services/ot-software/it-workflow-management-software/
…German Bundeswehr and responsible for the compliance of IT security in weapon systems. In addition to a few years of consulting, I have also been IT manager in a publishing house, which had an office area as well as a production area for printing and dispatching newspapers. I also had…
https://www.ondeso.com/en/article/the-we-is-ondeso-peter-lukesch/
…Therefore, we have decided to postpone the celebration and to set up a digital anniversary platform following the rules of distance. We would like to take this opportunity to thank all employees, customers and partners for the good cooperation of the last years and are very pleased about all digitally…
https://www.ondeso.com/en/article/10-years-ondeso/
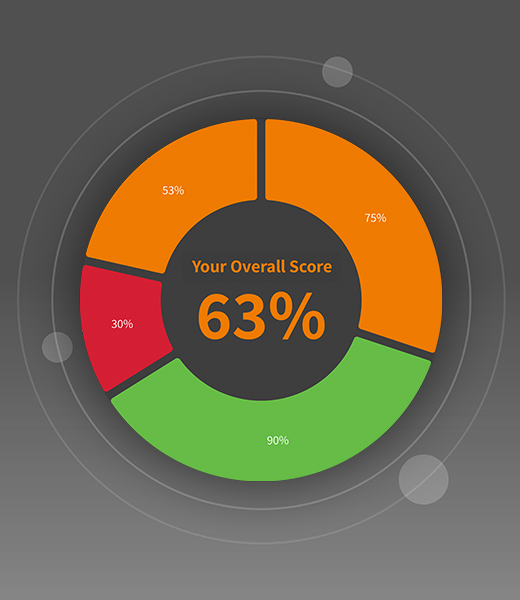
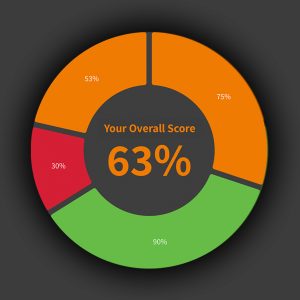
Compliance requirements, new laws and the growing threat of cyber attacks present significant challenges for plant operators, equipment suppliers and machine and plant manufacturers when it comes to OT management. Our OT administration software helps you to proceed in a structured and resource-efficient manner….
https://www.ondeso.com/en/
…description of the vulnerability. It also lists the Common Platform Enumerations (CPEs) that are directly and indirectly affected, the Common Vulnerability Scoring System (CVSS), if available, and the date and time of publication and last processing. The CWE is a unified naming tool for identifying and defining causes of the…
https://www.ondeso.com/en/article/common-vulnerabilities-and-exposures-cve/
As soon as assembly of the facility begins at the equipment manufacturer’s site, the operator needs to prepare the required infrastructure and implement or adapt last minute details such as network addresses, communication paths, and integration into the company process. Defined and standardised processes for these tasks are helpful….
https://www.ondeso.com/en/solutions/by-market/ondeso-ot-for-operators/
…all OT clients from Microsoft Windows XP and ends with the controlled management of end-of-life OT clients. Creating and restoring backups, rolling out security patches and centrally assigning configurations are other important workflows that can be automated and give you full control over the lifecycle management of your OT clients….
https://www.ondeso.com/en/ot-endpoint-management/industrial-it-workflow-automation/
…software developed by Siemens for the commissioning and maintenance of SIMATIC devices and is mainly used for PLC control, for example for setting up, configuring and querying SIMATIC parameters. The SIMATIC Assessment Suite – Data Collector, formerly SIMATIC Diagnostic Tool, is a software developed for troubleshooting and analysing SIMATIC devices….
https://www.ondeso.com/en/ot-endpoint-management/production-it/pcs7-software/
…sector and companies were also selected as targets. Attacks on think tanks and NGOs were also new this year. Distributed denial of service (DDoS) attacks were also carried out again. This type of overload attack on Internet services has been around for more than 20 years and it is already…
https://www.ondeso.com/en/article/status-of-it-security-2021/
…risks if necessary and to initiate countermeasures. Those who proactively implement uniform measures and, if necessary, can react promptly have the best chances. In the worst of all cases, this may involve restoring an up-to-date backup. References [1] https://www.bsi.bund.de/SharedDocs/Downloads/EN/BSI/Publications/Securitysituation/IT-Security-Situation-in-Germany-2019.pdf?__blob=publicationFile&v=3 [2] https://www.bsi.bund.de/DE/Presse/Pressemitteilungen/Presse2019/Emotet-Warnung_230919.html [3] https://www.bsi-fuer-buerger.de/BSIFB/DE/Service/Aktuell/Informationen/Artikel/emotet.html [4] https://elisa.tech/ [5] https://www.kritis.bund.de/SubSites/Kritis/EN/Home/home_node.html [6] https://www.bsi.bund.de/DE/Themen/KRITIS/IT-SiG/Was_tun/Stand_der_Technik/stand_der_technik_node.html…
https://www.ondeso.com/en/article/status-of-it-security-at-the-shop-floor-in-2019/