“It is not only the number of security incidents that is worrying, it is also the rapid development of new and adapted attack methods, the mass exploitation of serious software vulnerabilities, and the sometimes serious consequences that successful cyber attacks trigger.” This quote from Arne Schönbohm, President of the German Federal Office for Information Security (BSI), shows that the IT security situation remains “tense to critical” this year. As in previous years, we provide you with a summary of this year’s situation report [1] and look in particular at the impact on the industrial environment.
Survey period June 2020 – May 2021

Here you can find the report from the previous year, in which, among other things, the emotet infection process is explained in more detail.
As suspected in the BSI 2020 IT security report, the COVID-19 pandemic also had a significant impact on the IT world in the survey period June 2020 to May 2021, both in a positive (drivers of digitization) and negative (cyber attacks) sense. In the area of cyber attacks, no completely newly developed attack methods could be identified in relation to the pandemic, but phishing and social engineering attacks, among others, were thematically adapted to it. Fake products, including protective equipment, were also circulated, and there were increased attacks on drug agencies, vaccine manufacturers, or hospitals.
Looking at the big picture, the BSI classified the IT security situation in the period under review as “tense to critical”. One of the reasons for this were the expansion and increase in the use of extortion methods in cybercrime. Both hush money and ransomware, as well as protection rackets, could lead to network outages lasting days or weeks. In particular, hush-money extortion, in which the revelation of compromising information was threatened and carried out, increased. In the case of a hospital in North Rhine-Westphalia, no new patients could be admitted for 13 days because a blackmailer attack caused some central systems to fail. A Key for recovery was only released, when the authorities informed the attackers that they had attacked the university hospital instead of a university.
But it wasn’t just attacks like this that threatened IT security. Malware attacks also contributed. Compared to the previous year, the number of daily produced malware variants increased by around 22%. As this chart shows, there is a clear upward trend.
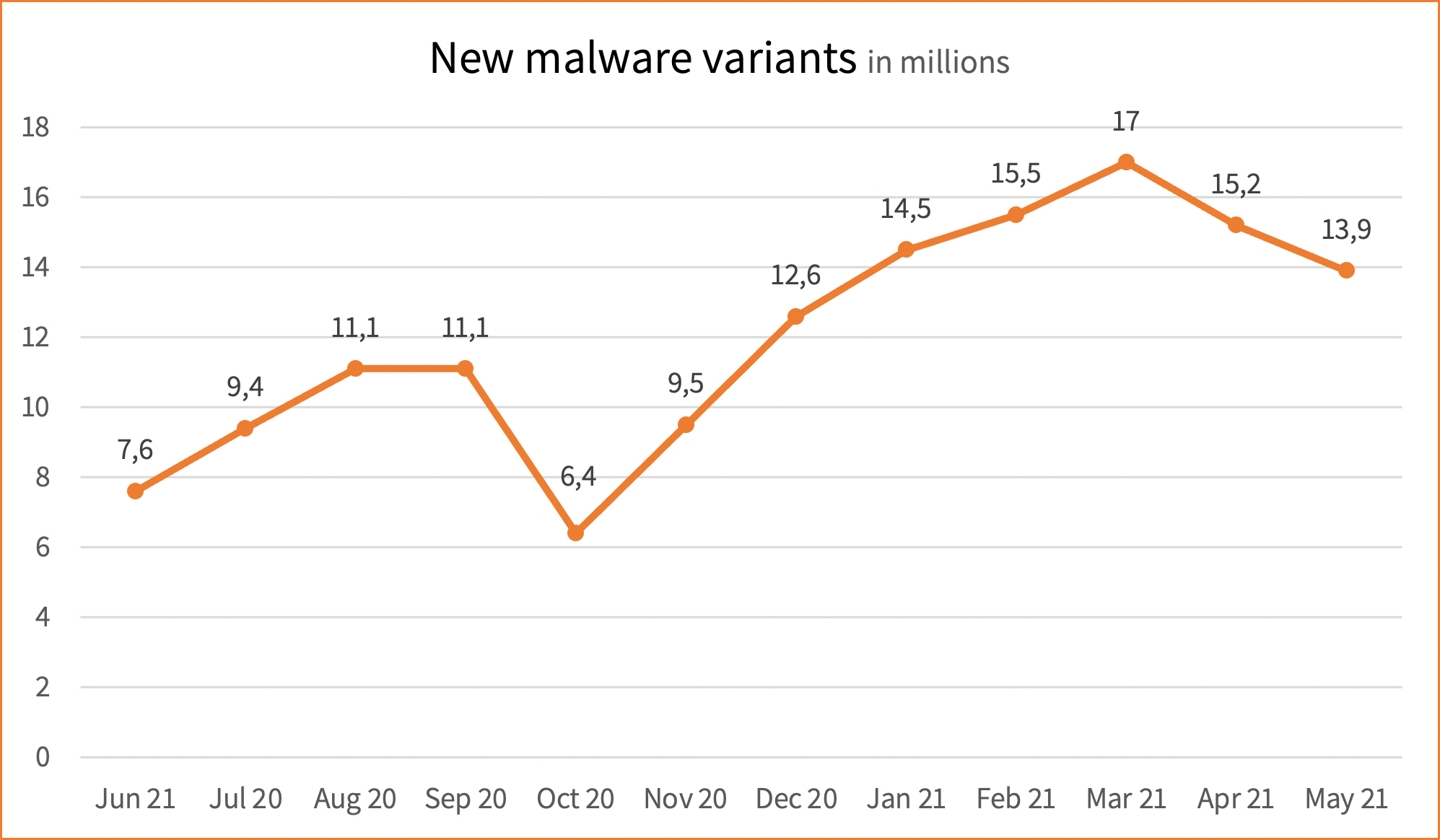
Picture: BSI IT security report 21
The takeover and destruction of the infrastructure for the emotet malware in January 2021 can still be considered a success, but it does not protect against future attacks with new methods. As a result of the takeover, more than 35 million data records collected with emotet were seized. However, the global damage caused beforehand is estimated at over 2.5 billion US dollars.
As can be seen from the example of the vulnerabilities in Microsoft Exchange, which are classified as “extremely critical”, vulnerabilities in the reporting period also represent an enormous threat and challenge. In the case of Microsoft, four vulnerabilities were closed in 2021 with an unplanned security update, which were immediately exploited when the issue became known. Approximately “98% of all tested systems in Germany” were vulnerable. 89% of them had carried out the necessary updates by May 2021 and were thus able to close the gaps. The remaining 9% are still vulnerable.
Advanced persistent threats (APTs) were also among the attack methods used in the period under review, although the motive and the great effort involved in the lengthy planning process set them apart from other methods. In most cases, perpetrators scan servers or use hard-to-control software supply chains as an attack path. This requires long and elaborate planning. In Germany, attacks in the observed period mainly targeted government agencies, but the defense sector and companies were also selected as targets. Attacks on think tanks and NGOs were also new this year.
Distributed denial of service (DDoS) attacks were also carried out again. This type of overload attack on Internet services has been around for more than 20 years and it is already possible to protect against it. Nevertheless, several million attacks occurred in 2020, which may have been aided by bandwidth expansion and the increased attack surface from home offices and homeschooling due to the COVID-19 pandemic. National and international companies, including CRITIS, were affected.
In the area of CRITIS environments, this IT security report falls into the same two-year detection cycle as the previous one. Therefore, there are few new findings to report. A total of 1,805 deficiencies occurred in the telecommunications, information technology, water and energy, and finance and insurance sectors. A small overview of the main deficiencies can be found here:
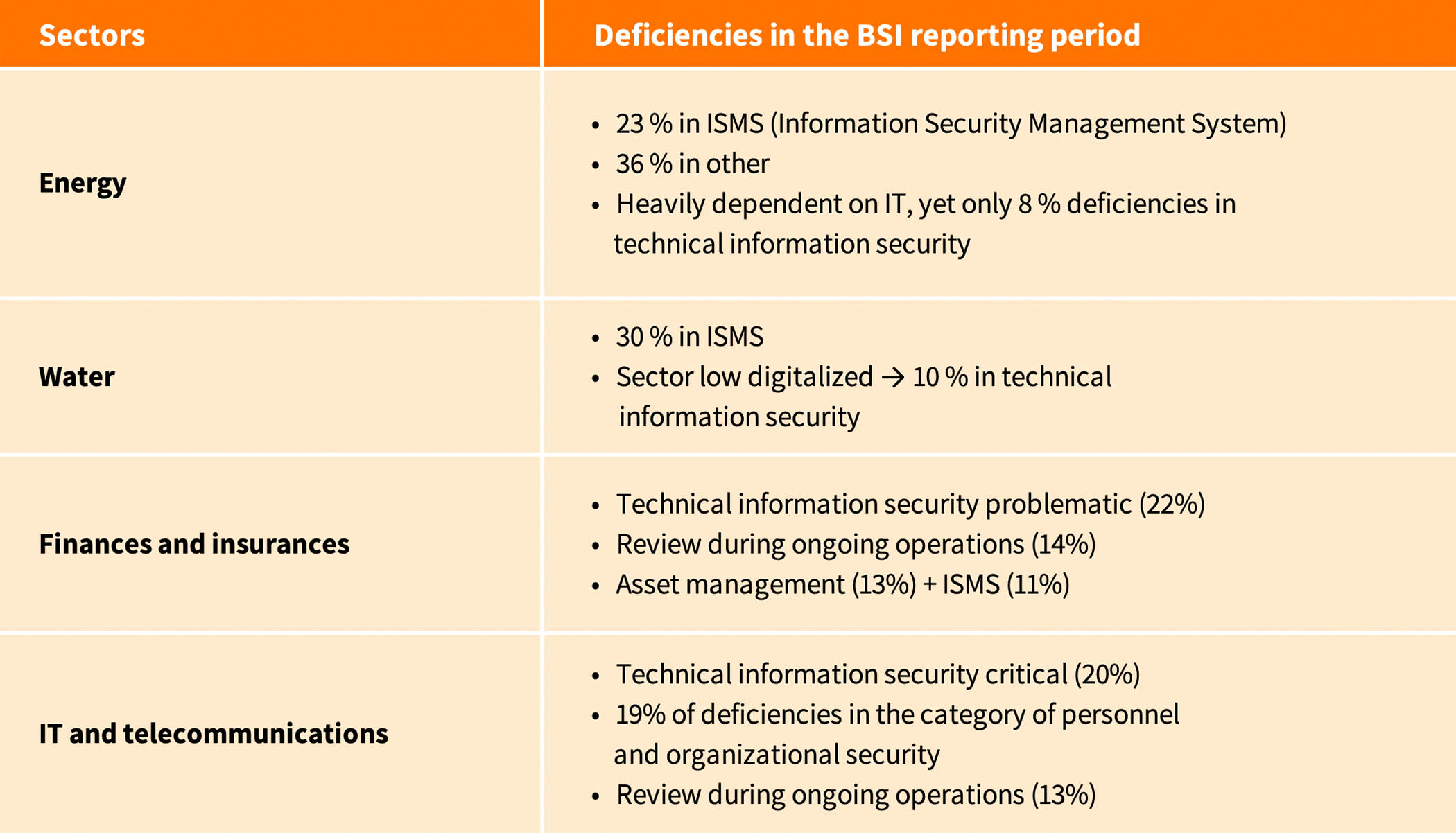
This year’s BSI report on the state of IT security again showed that the COVID-19 pandemic was a major driver of digitization in the period from June 2020 to May 2021. However, this was accompanied by undesirable side effects, as suspected in the previous year. Serious attacks on companies, institutions or private individuals could even jeopardize their existence. In such situations, it is often possible to react too quickly with stopgap solutions to avert a problem in a hurry. Here, the BSI recommends not putting functionality above security. As a positive example, they cite the Corona warning app, which has so far been functional and secure despite being put into operation quickly.
The motto “security over functionality” can even develop into a competitive advantage for companies in the area of cyber security in the workplace. After all, security creates trust and leads to acceptance, as the BSI explains using the example of autonomous driving.
Looking into the future, the threat of cybercrime will not diminish. Without concrete IT security measures, companies will continue to be threatened and suffer revenue losses or even insolvency. The example of Microsoft Exchange servers mentioned above, where 98% of all servers were vulnerable, showed how quickly this can happen. Even production is not protected against such attacks without regular patching and other measures. This trend could cause a loss of trust in modern technologies and digitalization, which should be avoided. Because as Ms. Merkel said, “Digitization and information security belong together. We need to be strong in both areas. That will essentially determine how successful Germany will be in the future.”
Would you like to compare the development of the management report with the previous ones? Here you can read our summary of the IT security management report 2020 and 2019:
Status of IT security at the shop floor in 2020
Status of IT security at the shop floor in 2019
You need help with the secure implementation of your production IT?
Contact us, we will help you!

Would you like to learn more? Do not hesitate to contact us, we will be happy to help you.


Here you can learn more about our company and our expertise as a pioneer and market leader.